Mobile app security: Why you need it and how to get it


In this day and age, mobile apps are literally everywhere. They offer convenience and connectivity to people around the globe, but they also represent a serious security risk. With the widespread use of smartphones, laptops and tablets, it’s crucial for businesses and digital service providers to understand why mobile app security is essential, and how to implement it in the most efficient way. In this article, we’ll explore its importance, as well as the best practices for keeping all the important data shielded.
What is Mobile App Security?
MAS refers to the measures taken to protect mobile applications and any information they handle from unauthorized access, disclosure, disruption, modification, or destruction. It includes protecting the code, as well as the communication between the actual product and any backend services it may connect to. MAS also includes protecting the user’s device. It is important because smartphones are now a critical part of our private and professional lives. They store and process our personal and financial details, and are often used to log in into banking services, corporate networks and other systems.
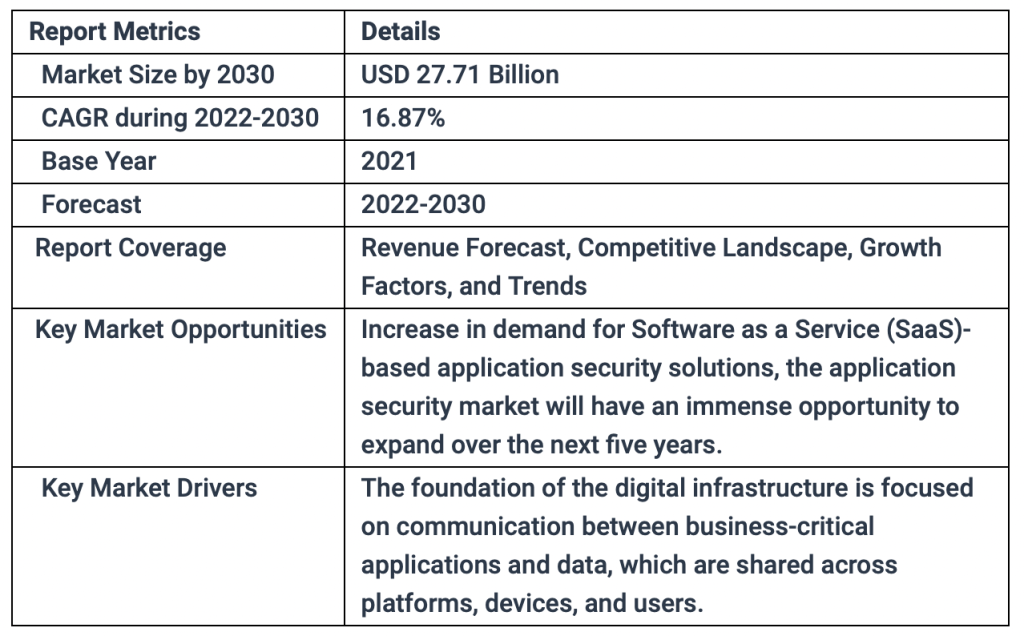
According to a report by MarketsandMarkets, the global MAS market size is expected to grow from USD 3 billion in 2019 to USD 7.2 billion by 2024. And it looks like the tendency is not going to change any time soon. According to this research, the global market for MAS is predicted to attain a valuation of around USD 27.71 Billion by the end of 2030.
If your product has a weak security level, it will likely be vulnerable to a variety of attacks. Some examples of potential consequences include:
- Data breaches: If an attacker is able to view sensitive info (such as login credentials or financial details), they may be able to steal it eventually.
- Malware infections: you make it easier for attackers to install malware on a user’s phone, which steals important personal info, sends unwanted messages or makes calls, or even takes full control of the gadget which is the worst scenario.
- Attackers may find personal details to make purchases or transactions, withdraw money, or perform other actions that significantly harm the smartphone owner.
- If such a breach occurs, it may also damage the gadget owner’s reputation or a brand’s image.
Note that such threats are constantly evolving, and even a program that was once considered secure at the time of its release may become vulnerable over time. Remember: hackers do not have a rest!
How to tell if an app is 100% secure?
There are several ways to find it out:
Many app stores and organizations offer certifications for apps that meet certain security standards. These certifications give visitors an idea of how secure a specific product is, but they may not cover every aspect so additional “investigation” is required.
Before installing an application, people should check the permissions it is requesting. If it is asking for permissions that are not necessary for its intended functionality, it could be a red flag.
The research of the developer’s brand, background and experience is also very helpful. A reputable company is more likely to have secure products and strong reputation.
Feedback from other people and experts also gives visitors an idea of the app’s stability and overall security. Moreover, if it has not been updated in a while, it may be a sign that the developer is not keeping up with the latest threats, so any issues are possible.
Users often download special software to scan their phones for potential threats. For instance:
- Lookout Security & Antivirus scans for viruses and other kinds of malware in addition to offering backup creation and remote device locating services.
- Kaspersky also offers a powerful tool for proactive defense with an integrated antivirus, firewall, privacy guard, parental controls and more.
Top App Security Tips
To avoid any potential harm, it’s essential to be aware of possible risks and how to combat them effectively. Here are proven tips to implement right now!
Use secure coding practices
These are a set of guidelines for identifying and eliminating potential security flaws during the development process. They help to ensure that mobile apps are built with security standards in mind, reducing the risk of attacks. Follow these rules to protect your product:
- Validate all input, including user input and data from external sources, to be sure it is in the expected format and does not contain any malicious code.
- Handle errors and exceptions properly to prevent the crashing and to minimize the amount of information an attacker may get from the error message.
- Implement strong authentication and access control mechanisms to prevent unauthorized access.
- Choose HTTPS or SSL protocols to encrypt data in transit and prevent eavesdropping or tampering.
- Implement secure session management techniques, such as session timeouts and session tokens, to protect against session hijacking.
- Use code signing to ensure that it has not been tampered with and to establish the identity of the developer.
- Avoid hardcoding sensitive information, such as passwords and keys, in the app’s code plus conduct its regular reviews.
- Stay up-to-date with the latest security trends, and apply any relevant patches as soon as possible.
Use encryption
It is the process of encoding data so that it is only accessed by an intended recipient. Encryption generally uses a key for both encrypting and decrypting processes, making it much harder for attackers to steal financial info and other personal details. Statistics says that 7 million unencrypted data records are compromised every day, according to this report by Varonis, so the situation must be changed.
There are several types of encryption:
- Symmetric one where the same key is chosen for both encrypting and decrypting.
- Asymmetric one where a pair of keys (a public and a private one) are chosen.
- Hashing is a one-way encryption method that creates a fixed-length output from a variable-length input. Works best to securely store passwords, for example.
- File-level encryption encrypts files at rest, such as on the device storage or on a remote server.
- Transport-level encryption encrypts information in transit, such as when it’s sent over a network.
Implement secure authentication mechanisms
These are methods of providing user access to a system while protecting the confidentiality, integrity, and availability of data. Such authentication mechanisms besides encryption include:
Multi-factor authentication (MFA): This mechanism requires visitors to provide more than one type of credential in order to gain access, such as a combination of something they know (e.g. a password), something they have (e.g. an authorization token sent via SMS) and/or something they are (e.g. biometrics).
Single sign-on (SSO): This is when users only have to log in once with their credentials in order to access multiple applications or services simultaneously, without having to re-enter their credentials for each one.
Access control lists (ACLs): These enforce strict rules around who is able to view what information and which actions they take within a program or on a network.
Limit app permissions
App permissions are requests for access to certain features or personal details on a device. Limiting them is good for app security because it helps to reduce the attack surface. When an app requests permissions that are not necessary for its intended functionality, it increases the chances of a malicious actor finding and exploiting product vulnerabilities. So, if an attacker is able to exploit such a vulnerability in an app that has access to sensitive info, they could steal it.
Additionally, it helps to protect user privacy. When an app requests unnecessary permissions, it may collect and use personal data without the owner’s knowledge or consent.
Keep your app up to date
Regularly make updates as they often contain essential security patches and bug fixes. Additionally, it’s important to update applications quickly as loopholes are found in outdated versions more easily. Developers may also use updates to add new features that improve the functionality, improving its resistance to any digital dangers.
Hire a mobile app security expert if needed
Hiring an expert may be beneficial because they possess the necessary expertise to assess and identify potential risks that could impact a product. They review code, test for vulnerabilities, and apply best practices that meet industry standards and regulations. Additionally, they are usually well informed about the current threats and give up-to-date relevant advice on how to secure your product more effectively.
How to find the best candidate? Determine what type of expertise you require, such as proven experience with encryption, secure coding practices, or vulnerability assessments. Then, look for professionals with relevant experience and related certifications such as Certified Information Systems Security Professional (CISSP) or Certified Information Systems Auditor (CISA).

Check the candidate’s portfolio of past work properly and speak with their references/previous clients to find out if they have a solid track record of success in the area you are most interested in.
Have a strong API strategy
APIs provide the connection point between applications and external data sources, which makes them vulnerable to misconfiguration and malicious attacks. A robust API strategy will help protect against these dangers by mitigating risks through access control, authentication, authorization, logging, intrusion detection, encryption, and other forms of protection. Additionally, a strong API strategy allows for better organization of APIs within an application’s architecture to ensure that they are secure while still being accessible to authorized users. Use authentication methods such as OAuth or JSON Web Tokens (JWT) to ensure that only authorized users have access to your API.
Furthermore, validate all input data to ensure that it meets the requirements of your API and that it is free of any malicious content. Use HTTPS to encrypt all communication between the client and the server to protect against man-in-the-middle attacks plus keep your API and any dependencies up-to-date to ensure any known vulnerabilities are patched.
Optimise Caching
Caching is a method of data storage that allows for faster loading times, as it is stored locally and not fetched from a server every time. It works by saving frequently used data onto the device and retrieving it when needed, thus reducing waiting times. For example, when using Google Maps or an online shopping application, the map tiles or product images are saved locally for future access. This helps improve the user experience by making a product more responsive and efficient.
What should app development specialists use/implement to optimize caching?
- A caching library or framework, such as OkHttp or Retrofit, to handle it automatically.
- A key-value store, such as Realm, to do it locally on the gadget.
- LRU algorithm to evict old or less frequently used data from the cache.
- Caching headers, such as ETag or Last-Modified, to determine if cached info is still valid.
- Compression to reduce the data amount that needs to be cached and transferred.
- A cache eviction policy.
- A combination of client-side and server-side caching.
- A background task scheduler to refresh data in the cache regularly.
Make sure to test your strategy and fine-tune it based on the usage patterns.
Perform Penetration Testing
It is a process used to evaluate the app security by attacking it to identify potential weaknesses. By utilizing techniques such as fuzzing, reverse engineering, or code injection, testers are able to detect flaws within the code and provide recommendations for remediation. Such testing should be conducted regularly to ensure that the product is constantly monitored for any threats and quickly patched with updates if any issues are discovered.
For Corporations: Consider Device Theft Action Plan
Every year, thousands of phones are lost or stolen around the world, leaving the sensitive data they typically contain vulnerable to being stolen. Speaking about corporate devices, to reduce this risk, IT departments should provide a remote wiping feature to remove any stored confidential info on a stolen company smartphone. Even better, a corporation can minimize such risk by implementing policies that ensure no personal or confidential information is ever stored on devices in the first place.
Prevent such an unpleasant situation by following these steps:
- Use a password or PIN: requiring it to unlock a smartphone or a laptop adds an extra protection layer.
- Use device tracking software as it helps to locate and remotely lock it.
- Limit access to files on the device by implementing remote access controls to prevent any unauthorized activity.
- Regularly back up files to a secure location, so you can restore it later.
- Notify your IT department immediately if your device has been lost.
- Check your accounts for any suspicious activity and change your passwords.
If a theft happened, report it to the authorities and provide them with the device’s IMEI number and identifying details as soon as possible.
Conclusion
It’s vital to take the necessary steps to ensure your data remains safe. Taking measures such as encrypting the information, setting up authentication protocols, patching vulnerabilities as they arise and implementing backup processes all help protect your products from malicious attacks. By following these best practices, businesses can rest assured that their customers’ details are protected.
Ein-des-ein guarantees the security of your product
Ein-des-ein is a mobile design and development company. We provide mobile development services and our specialists utilize modern frameworks and follow coding standards so they know how to make an app that is both reliable and nice-looking. Furthermore, we have rigorous testing processes in place to make sure that they are bug-free and perform well on different devices. It does not matter which platform you choose, our experienced team specializes in both android development and ios app development as well as UI/UX design. Here are some of the benefits you get when you hire the EDE team:
- Comprehensive code reviews and automated testing to ensure secure coding practices are followed and there are no vulnerabilities in the system.
- Secure data storage with encryption, multi-factor authentication, and access control protocols in place.
- End user privacy is protected with tools like GDPR compliance, HIPAA compliance, and data masking.
- Advanced security protocols for protecting against malicious attack vectors such as DDoS attacks, phishing attacks, SQL injections, etc.
Our agile methodology allows us to quickly iterate and make changes based on customer feedback. We provide personalized attention throughout the process, from initial consultation to launch and post-launch support. Contact us now by following this link so we could estimate your project!



